Security testing is a key in ensuring that information systems, applications, and data are protected from potential threats and attacks. Here are some of the main reasons why security testing is an important step in developing and maintaining any IT systems:
- Identifying vulnerabilities: Security testing identifies potential weaknesses in a system that attackers can exploit attacks. This includes analyzing software, network infrastructure, and other system components for possible vulnerabilities.
- Preventing attacks: By identifying and addressing vulnerabilities before they are actively exploited by attackers, security testing helps prevent possible attacks and minimize security risks.
- Protecting data confidentiality and integrity: Security testing helps protect confidential data and maintain its integrity. This is especially important when sensitive personal or corporate data is being processed.
- Compliance with legislation and regulations: Many industry standards and legislation require compliance with certain security standards. Security testing helps ensure compliance with such regulations and prevents potential fines or loss of reputation.
- Increase user confidence: Users and customers expect their data to be secure. Security testing helps organizations demonstrate their willingness and ability to keep information secure, which builds user trust.
- Maintain business continuity: Conducting security testing helps prevent potential system failures caused by attacks or other events that could disrupt normal business operations.
The overall result of security testing is the creation of more resilient and reliable information systems, which is essential in today’s digital environment.
Types of security testing professionals
Security testing can be performed by a variety of experts and organizations that specialize in information security. Here are a few types of experts who can perform security testing:
- Ethical Hackers (Penetration Testers): These experts attempt to hack into a system using the same techniques as potential attackers to identify vulnerabilities and prevent potential attacks.
- Application Security Experts: These professionals focus on software and application security by checking code for vulnerabilities.
- Network Security Experts: Network security experts analyze network infrastructure, identify potential threats, and develop measures to prevent them.
- Data Security Experts: These experts assess the protection and processing of data and verify that systems meet confidentiality and integrity requirements.
- Information Security Analysts: They provide overall security oversight of information systems, analyze threats, and develop protection strategies.
- Compliance Specialists and Security Auditors: These professionals assess a system’s compliance with laws, regulations, and security standards.
Security testing can be performed either by internal company employees or by external specialized firms. External experts often provide a more objective assessment because they are not part of the internal system development or support team.
How to conduct security testing if there is not enough budget for individual specialists
Conventional testers who specialize in functional or automated testing can also contribute to software security. While their primary area of expertise may be in functional testing, they can perform a number of activities to identify underlying vulnerabilities.
Here are a few ways that regular testers (QA engineer) can incorporate security elements into their work:
- Input testing: Testing for correct data entry processing can help identify vulnerabilities related to injections such as SQL injection or code injection.
- Testing for invalid operations: Checking the system for invalid operations processing and data validation can help identify security issues.
- Session and authentication testing: Verifying that authentication mechanisms, aswell as session processing, are working properly can help identify unauthorized access vulnerabilities.
- Access level testing: Checking for adherence to minimum privilege principles and scrutinizing user access rights.
- Code security analysis: While this can be a more complex task, testers can scrutinize code for potential vulnerabilities.
- Network security testing: Checking how the system interacts with the network and detecting potential risks such as unencrypted communications.
- Use of security tools: Testers can use specialized tools to perform basic vulnerability scanning and security analysis.
- Adhering to security best practices: Checking whether the application or system being developed complies with basic security principles such as password protection, encryption, etc.
While these steps may be basic and do not replace full-fledged security testing, they provide an opportunity for regular testers to emphasize security aspects and help identify the most obvious vulnerabilities.
The most popular security testing tools among QA engineers
Below are brief descriptions of a few popular tools:
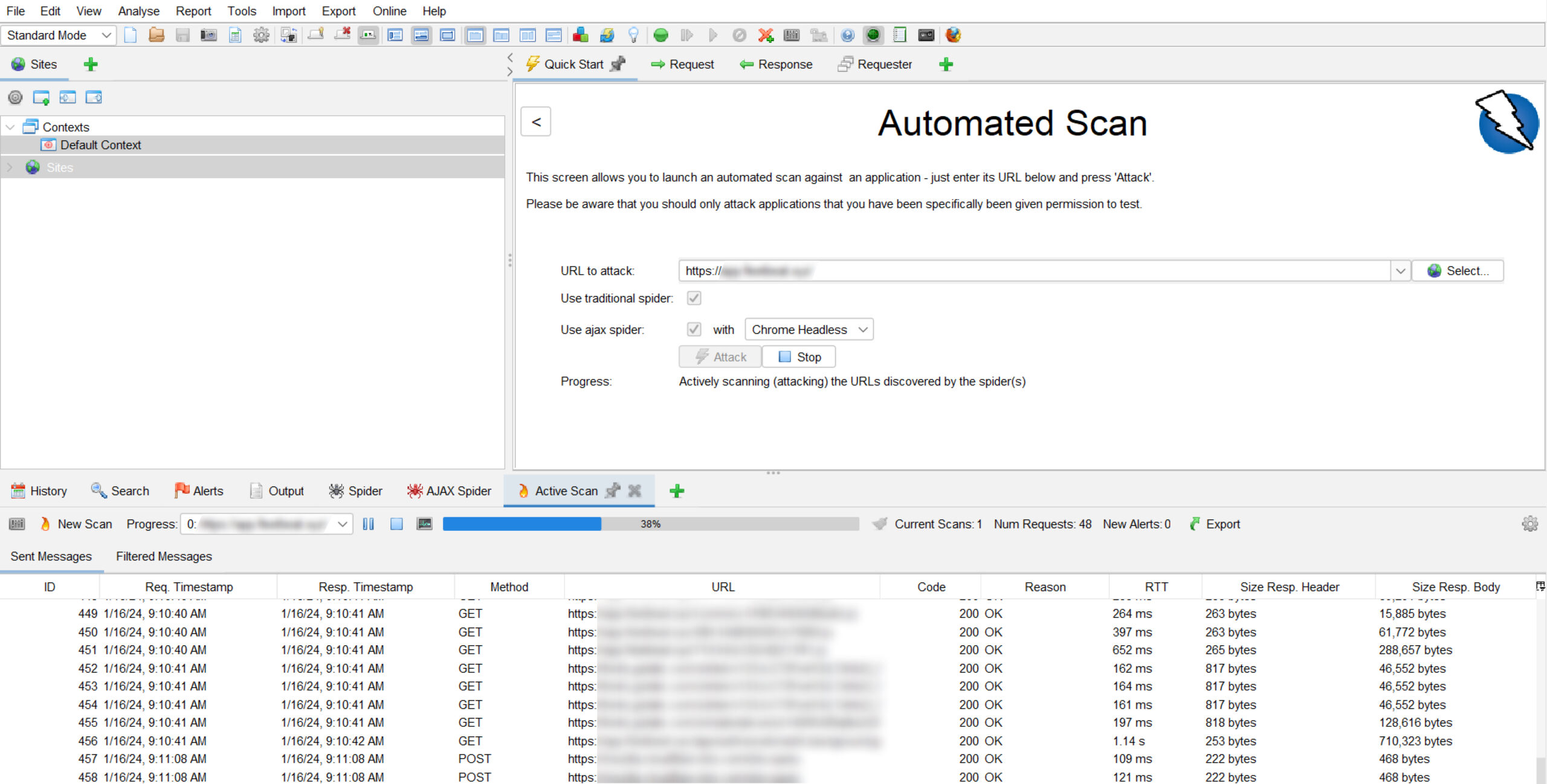
- Burp Suite is an integrated suite of tools for web application security testing. It includes vulnerability scanning, traffic analysis, request hijacking, and more. Also, Burp Suite is often used for session and authentication testing.
- Metasploit is a platform for developing, testing and utilizing exploits. It provides an extensive database of exploits and allows you to test systems for vulnerabilities.
- Nmap (Network Mapper) is a powerful network scanner that is used to discover devices on a network and identify open ports and services.
- Wireshark is a network traffic analysis tool that allows you to view and analyze data transmitted over a network.
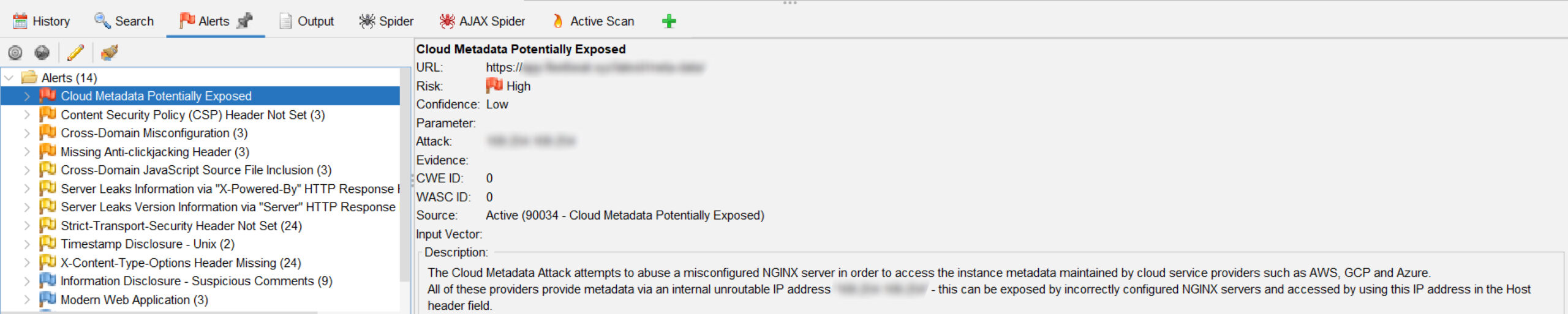
- OWASP ZAP (Zed Attack Proxy) is a web application security scanning tool from the Open Web Application Security Project (OWASP). It provides automated vulnerability testing features and can be used to detect web application vulnerabilities such as cross-site scripting, injections, and more.
- Snor is an intrusion detection system (IDS) that analyzes network traffic for suspicious activity. It can detect real-time attacks such as hacking attempts or network anomalies.
These tools provide basic security testing capabilities, and their selection depends on the specific needs of the project and testing objectives.
Conclusion
Security testing is very important even at a basic level. In the absence of dedicated budgets for pentester teams or third-party audits, you can engage teams of in-house testers who will be able to superficially analyze and test functionality and server interaction. However, it should be understood that such actions can reduce the risks of hacking, but do not guarantee complete security at all.
At IT-Dimension, we are ready not only to assess your project but also to offer an individualized approach. Our experts will select optimal testing methods, taking into account your budget, timeline, and unique requirements.
Contact us today to get a professional consultation!